共计 2504 个字符,预计需要花费 7 分钟才能阅读完成。
升级1.70,出现这个错误:
[php]Fatal error: Call to undefined function libxml_disable_entity_loader() in /app/code/core/Zend/XmlRpc/Response.php on line 179
[/php]
解决办法是:
The Issue
The vulnerability potentially allows an attacker to read any file on the web server where the Zend XMLRPC functionality is enabled. This might include password files, configuration files, and possibly even databases if they are stored on the same machine as the Magento web server.
Solution
We recommend that all Magento implementations install the latest patch appropriate for your platform:
Magento Enterprise Edition and Professional Edition merchants:
You may access the Zend Security Upgrade patch from Patches & Support for your product in the Downloads section of your Magento account. Account log-in is required.
Download
Magento Community Edition merchants:
Community Edition 1.4.0.0 through 1.4.1.1
Community Edition 1.4.2.0
Community Edition 1.5.0.0 through 1.7.0.1
Applying the patch via SSH
Here is an example as to how to apply the patch file via SSH for a 1.4 store
cd /home/mystore/public_html
wget -qO - http://www.magentocommerce.com/downloads/assets/1.7.0.2/CE_1.4.0.0-1.4.1.1.patch | patch -p0Applying the patch by replacing the file
If you are unsure as to how to patch the files using the command line, we have pre-patched the files for the relevant version for your convenience, so you can download the file and replace as effected. We cannot upload the Enterprise patch – but if you get in touch, we would be glad to help.
Community Edition 1.4.0.0 through 1.4.1.1
./lib/Zend/XmlRpc/Request.php
./lib/Zend/XmlRpc/Response.php
Community Edition 1.4.2.0
./lib/Zend/XmlRpc/Request.php
./lib/Zend/XmlRpc/Response.php
Community Edition 1.5.0.0 through 1.7.0.1
./lib/Zend/XmlRpc/Request.php
./lib/Zend/XmlRpc/Response.php
Please note. This is only suitable if you haven’t made any modifications to this file.
Workaround
If the patch cannot be applied immediately, the following instructions can be followed to temporarily disable the RPC functionality that contains the vulnerability. Please be advised, any integrations that rely on the XMLRPC API functionality will no longer work after this workaround is implemented.
1. On the Magento web server, navigate to the www-root where Magento app files are stored.
2. In the wwwroot, navigate to /app/code/core/Mage/Api/controllers.
3. Open XmlrpcController.php for editing.
4. Comment out or delete the body of the method: public indexAction()
5. Save the changes.
Additional Notes
Users with existing IDS capability may monitor the RPC interface to watch for attacks. As always, we recommend maintaining an up-to-date installation of the Magento platform as the best way stay secure.
The latest releases of Magento (Community Edition 1.7.02 and Enterprise Edition 1.12.02) incorporate the appropriate patches. please use correct versions of releases 1.7.0.2 and 1.12.0.2 .












 多乐士
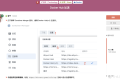
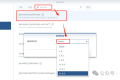
通过摸索发现ssh拉取会报错,直接网页访问下载会报404错误,不知道原因;但是可以通过群晖CM注册表访问下载,其方法如下:
Container Manager-注册表-设置-新增-注册表名称随便写,注册表URL填你的加速地址,勾选信任的SSL自我签署证书,登录信息不填-应用-使用你的地址,这是注册表会显示了,在搜索栏中输入映像名称,搜索结果在每一页的最后一个,你需要划到最后一个进行下载,实测可正常下载安装。
以上供网友参考。
多乐士
通过摸索发现ssh拉取会报错,直接网页访问下载会报404错误,不知道原因;但是可以通过群晖CM注册表访问下载,其方法如下:
Container Manager-注册表-设置-新增-注册表名称随便写,注册表URL填你的加速地址,勾选信任的SSL自我签署证书,登录信息不填-应用-使用你的地址,这是注册表会显示了,在搜索栏中输入映像名称,搜索结果在每一页的最后一个,你需要划到最后一个进行下载,实测可正常下载安装。
以上供网友参考。